Encryption Key Windows 8 downloads - Free Download Windows 8 Encryption Key - page 16 - Windows 8 Downloads
... volumes within a file or a hard drive. Encryption and decryption are made on the fly, allowing ... Supports AES-256, Serpent and SHACAL-2 ciphers. - Cascade encryption with free choice of the ciphers. - Supports ...
Price: FREE / Freeware
... supported password decoding methods, * Adobe Photoshop License Key Decoder * Base64 Password Decoder * Bat! Password Decoder * Cisco ...
Price: FREE / Freeware
... encrypted SQLite database* - Verify an encrypted database's encryption key - Change the encryption key for an encrypted database * In order ...
Price: $8.00 / Shareware
... first browser integrated security and privacy management console. Key Features: * Active Anti-Virus - Stop viruses and ... blocks online tracking pixels and cookies * HTTPS Encryption - Ensures encrypted website communications when supported * ...
Price: FREE / Freeware
... first browser integrated security and privacy management console. Key Features: * Active Anti-Virus - Stop viruses and ... blocks online tracking pixels and cookies * HTTPS Encryption - Ensures encrypted website communications when supported * ...
Price: FREE / Freeware
... your email address to obtain a valid license key. 3. Simply fill in the required information. ... then receive a confirmation mail including your license key. 4. Once received, simply enter your key ...
Price: FREE / Freeware
Pidgin Password Decryptor is the FREE software to instantly recover account passwords stored by Pidgin Messenger. Pidgin is a Universal Instant ...
Price: FREE / Freeware
... the assigned safe directory. The AES-128 and AES-256 encryption algorithms ensure reliable protection. Virtual Safe Professional also includes a built-in ...
Price: $10.00 / Shareware
... on the password security configuration. Here are the key benefits ------------------------------------------------------- + Wi-Fi Password Recovery: Instantly discover & decrypt all ...
Price: $39.95 / Demo
... software with ease. Download free demo version first. Key features of SysInfoTools PST Recovery software are: * ... folder hierarchy during export process; * Support Outlook encryption to recover accurate data; * Provide fastest scanning ...
Price: $49.00 / Shareware
... totally cover all the needs. Total Backup Recovery Key Features Reliable system backup and protection (imaging) Full, ... server as a duplicated backup AES 256 bit encryption, compression, and password One-click system backup Universal restore ...
Price: $39.95 / Shareware
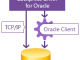
... and direct access to Oracle without Oracle Client. Key features of dbExpress drivers: * macOS & Linux ... Cloud (DBaaS) in the Direct mode * Oracle Encryption in the Direct mode * Oracle Data Integrity ...
Price: $229.95 / Shareware
... distribution, unauthorized users can not open them. Authorization key can be binding with end user's hardware, one device one key, specify its time interval and also blacklist feature ...
Price: FREE / Freeware
... you are trying to send. The program generates encryption images which hide your message before you can send. The send will have to receive the key generated upon message encryption before he or she ...
Price: FREE / Freeware
The Password Gorilla 64-bit helps you manage your logins. It stores all your user names and passwords, along with login information ...
Price: FREE / Open Source
... from the current profile location. Here are the key benefits, * Instantly scan and recover all stored FTP login passwords ...
Price: FREE / Freeware
Application for encryption and decryption of files with symmetric key. Features: * A non-standard type of encryption based on your own chaotic pseudo-random generator is ...
Price: FREE / Freeware
... DVD movies on your smart phone or tablet. Key Features: 1. Free rip any DVD Free DVD ... code, Sony ARccOS, UOP, RCE and the new encryption method - Disney X-project DRM. 2. Own comprehensive ...
Price: FREE / Freeware
... people's PDF documents with up to 256 bit key strength (AES). Add a password to open it so that users ...
Price: $19.90 / Shareware
... client systems. DWG to PDF Converter Command Line key features: * Convert thousands of files and keep ... of AutoCAD DWG and DXF files. * PDF encryption and password protection * Support Command Line operation, ...
Price: $199.00 / Shareware
Similar encryption key for Windows 8 keywords
encryption detector
encryption library c
encryption folder
encryption manager
encryption software 20 r
encryption freeware
encryption component
encryption key
encryption
encryption software 80 r
encryption library
encryption software 100 r
encryption program
encryption software 40 r
encryption sdk
encryption tool
encryption tools
encryption algorithm
encryption security software
encryption software
Windows 8 Coupons
-
MacX Media Management Bundle
70% Off -
EaseUS
20% off -
Media Player Morpher
85% Off -
WinX HD Video Converter
56% Off -
WinX DVD Copy Pro
42% Off
Saved Downloads
You have not saved any software.
Click "Save" next to each software.
Click "Save" next to each software.
Would you like to receive announcements of new versions of your software by email or by RSS reader?
FREE Registration Here!
Win8 Download Picks
Top Win8 Downloads
- iCare Data Recovery Software Enterprise
- Grand Theft Auto: Vice City Ultimate Vice City Mod
- CorelDRAW X7 (x64 bit)
- Universal Maps Downloader
- DMDE - DM Disk Editor and Data Recovery
- Privacy Eraser Free
- Paperless Printer
- WhatsApp for PC
- ProgDVB (64 bit)
- Money Manager Ex x64
- Ace Stream Media
- Blender - 64 bit
- Vladovsoft Fitorg
- PureBasic x64
- Disk Pulse Pro x64